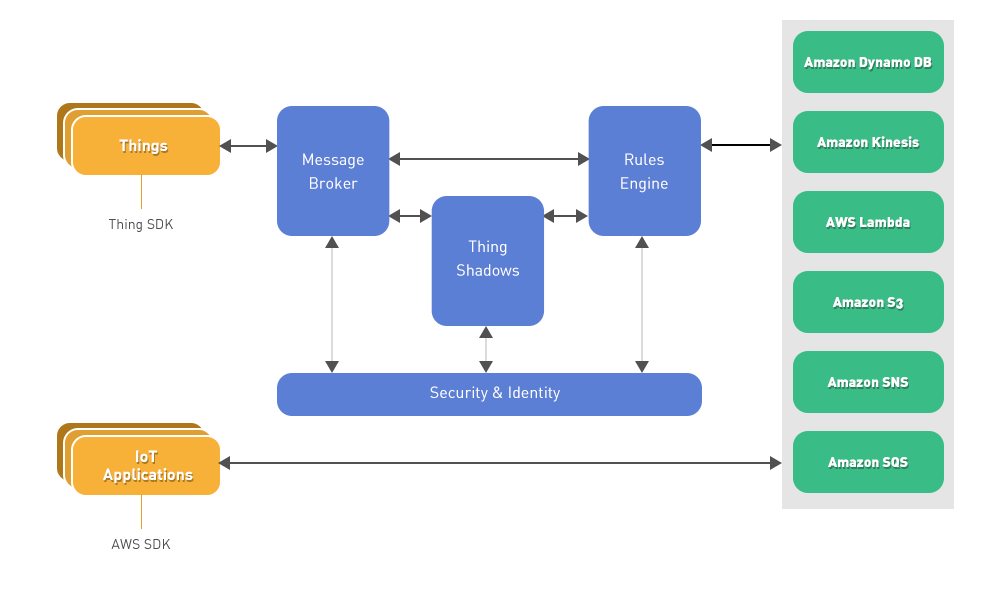
Components of AWS IoT
- Things are devices that are connected through IoT. Things have names, attributes, and shadows.
- Thing shadows are the state representations of things. They track the state of each connected device in AWS IoT.
- Rules engine performs message processing based on the expressions that you define. It integrates with other AWS services like Lambda, DynamoDB, and S3.
- Message broker gives a secure mechanism for things and AWS IoT applications to communicate with each other by publishing and receiving messages by MQTT or HTTP protocols.
- Device SDKs are client libraries developed for devices. The client libraries make it easy for applications to communicate between devices and AWS IoT Message Broker.
- Device gateway facilitates secure communication between devices and the AWS IoT platform. Authentication of each device is done by X.509 certificates.
- Thing registry establishes the identity of each thing and stores its metadata. The metadata helps us recognize the capabilities of the thing.
 AWS IoT Framework[/caption]
AWS IoT Framework[/caption]
AWS IoT Processes
The AWS IoT platform provides software tools to deploy your own IoT solutions. By providing a comprehensive IoT framework, it reduces application development time.Using the AWS IoT client libraries, the things connect to the AWS IoT platform on the cloud. Communication between a thing and the AWS IoT platform is secured through the use of X.509 certificates. Either we can use our own certificate or AWS IoT will provide the certificate. The certificate must be registered and activated with AWS IoT and copied onto the thing. The certificate acts as the credential when the thing communicates with AWS IoT. For successfully authenticated things, an entry will be created in the thing registry, which will be maintained at least for seven years from the last date of use of the thing.
The things publish their latest state onto the thing shadow in the cloud. The information is transferred using JSON format and can be published using MQTT protocol. Each MQTT topic has a name that identifies the thing whose state is being updated. The AWS IoT MQTT message broker will send all messages published on an MQTT topic to all clients subscribed to that topic.We can create rules that define actions to be performed based on the data in a message. For example, we can invoke a Lambda function or query DynamoDB table. Rules use expressions to filter messages. When a rule matches a message, the rules engine invokes the action using the selected properties. Rules also contain an AWS Identity and Access Management (IAM) role that grants AWS IoT permission to the AWS resources used to perform the action.
Each thing has a thing shadow that stores the state information. State information has two parts—the state last reported by the thing and the desired state requested by an application. An application can request the current state information for a thing. The shadow responds to the request by providing a JSON document with the state information, metadata, and a version number. An application can control a thing by requesting a change in its state. The shadow accepts the state change request, updates its state information, and sends a message to indicate that the state information has been updated. The thing receives the message, changes its state, and then reports its new state.
Connecting with AWS IoT
We can connect devices with AWS IoT in a few simple steps. Let's consider an automated parking slot management application. An infrared sensor connected to Raspberry Pi 2 can be the device that monitors occupancy of slots. When a vehicle arrives, the cloud-based application checks the state of the shadow to check for free slots and directs the vehicle accordingly.The key steps include:
- Creating a thing in AWS IoT and adding policies.
- Downloading embedded C SDK for the client.
- Downloading certificates for authentication.
- Creating thing shadow.
- Developing an AWS application to integrate with the device.
Conclusion
Having most of the common requirements of an IoT application as service and by providing an SDK for various common device platforms, the AWS IoT platform speeds up IoT application development and deployment. This facet of AWS IoT could soon see it become a part of our day-to-day life.