The Quest for an Alternative
We have always depended on middlemen to exchange values amongst ourselves. The ancient barter system was unscalable and had gaping holes of inefficiency. The monetary system that replaced it infused some stability to the exchange, but it came with its own share of problems. Fraudulent schemes and money laundering have become so commonplace, they don't shock us anymore. And there arose the question: Is there a safer alternative to the conventional banking system? A feasible alternative was put forward by Satoshi Nakamoto in 2008. He proposed a decentralized peer-to-peer cryptocurrency, the Bitcoin, which set the foundation for a technological revolution. However, the story doesn't end there. If Bitcoin is the crust of what was the proposed, the underlying Blockchain technology is the meat.Bitcoin gives us, for the first time, a way for one Internet user to transfer a unique piece of digital property to another Internet user, such that the transfer is guaranteed to be safe and secure; everyone knows that the transfer has taken place, and nobody can challenge the legitimacy of the transfer. The consequences of this breakthrough are hard to overstate.
—Marc Andreessen, Founder of Mosaic
Building Blocks of Blockchain
The Blockchain, for the most part, behaves just like your everyday database except that it has headers that are public. Anyone can verify the message you send as it has your signature, but only you can access the secure information stored within it. The basic building blocks of blockchain technology are the following:Transaction
It is the record of an event. It is stored in the blockchain permanently.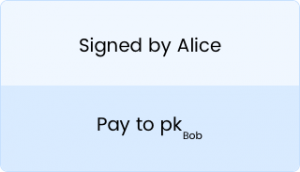
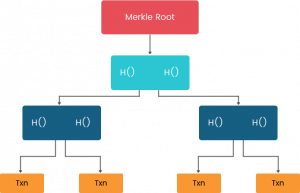
Blocks
A set of transactions are grouped together to form a block.
Hash Functions and Hash Pointers
Cryptographic hash functions are the backbone of blockchain technology. They provide the much-needed security by virtue of the following features:-
- They are collision-free. It means that it is impossible for the hashes of two different data to be equal. That is, ∄x≠y & H(x) = H(y).
- They are apt for data hiding. It would be nearly impossible to get back the data from its hashed form. That is, you can't get back the value of m from H(m).
- They are puzzle-friendly. This feature ensures that there are no shortcuts when these functions are used as puzzles. That is, if a puzzle such as H(k|x) = y is given, the only way to solve it should be by randomly finding the value of k.