- Decentralization
- Distributed Consensus Protocol
- Double-Spend Attack
- Proof of Work
- Incentive Mechanisms
Decentralization
There is no central repository of information in Bitcoin. The network maintains a shared distributed ledger among its nodes. Even though Bitcoin itself is decentralized, the software updating part (of Bitcoin) is decided by an elite group of developers. When the rules of the network are changed, software update takes place. Such an update should be reflected in all the nodes in the network or else there is a probability of a fork occurring. These forks result in alternate cryptocurrencies or “Altcoins” such as Bitcoin Cash, Bitcoin Gold, and so on.Distributed Consensus Protocol
Bitcoin, being decentralized, depends on distributed consensus protocol to maintain the blockchain. Whenever a new transaction is created, it is broadcast to the network. Bitcoin makes use of the distributed consensus protocol to bring consistency in:- Transactions that are broadcast
- Order in which the transactions happened
Double-Spend Attack
A double-spend is an attack where a given set of coins is spent in more than one transaction. Consider this transaction. Alice pays Bob for some service. The transaction contains Alice’s signature, Bob’s public key, and a hash. The hash points to the transaction from which Alice got the coins. It takes no effort to verify the details of the transaction. Alice broadcasts this transaction to the network.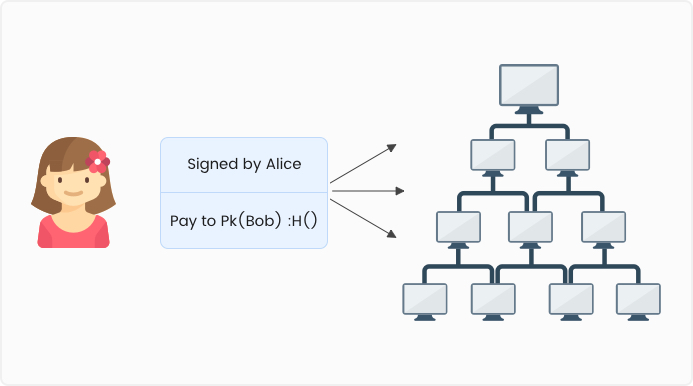 The nodes that receive this transaction will validate it and add it to their blocks.
The nodes that receive this transaction will validate it and add it to their blocks.
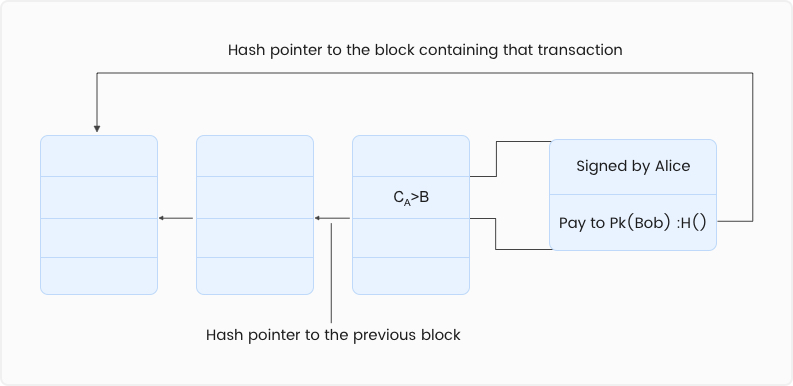 There might occur a situation wherein Alice uses the same coins in a different transaction. She might broadcast another transaction along with the previous one. In the fraudulent transaction, she could specify the receiver as herself.
There might occur a situation wherein Alice uses the same coins in a different transaction. She might broadcast another transaction along with the previous one. In the fraudulent transaction, she could specify the receiver as herself.
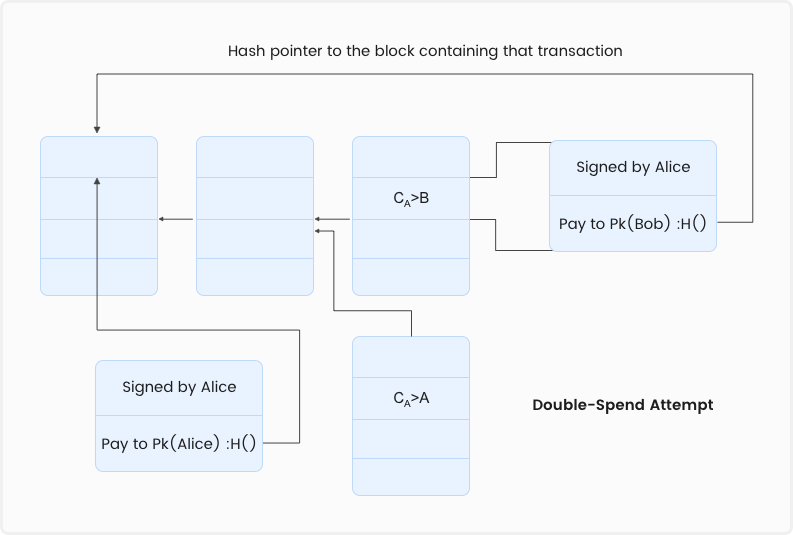 The coins in both the transactions will point to the same location. This is a classic example of a double-spending attack. Which of the two transactions will end up in the long-term consensus blockchain will depend on the number of confirmation each of them receives. Eventually one of the transaction will reach the consensus state. The other one will get rejected.
The coins in both the transactions will point to the same location. This is a classic example of a double-spending attack. Which of the two transactions will end up in the long-term consensus blockchain will depend on the number of confirmation each of them receives. Eventually one of the transaction will reach the consensus state. The other one will get rejected.
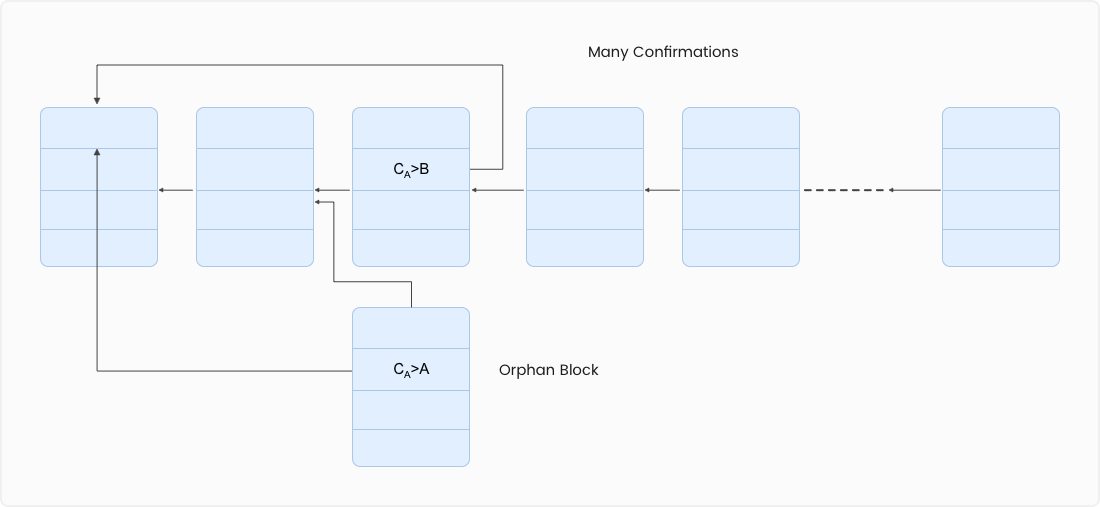
A block gets into the long-term consensus chain.
With time, the number of confirmations on the valid block increases. Higher the number of confirmations, higher the probability of the valid block ending up on the long-term consensus chain. When a block is added to the long-term consensus chain, the probability of it getting rejected reduces exponentially with each confirmation. Heuristically, it would be best to wait for six confirmations before a block is to be regarded as part of the long-term consensus chain.Proof of Work
The selection of a random node for proposing the next block plays a crucial role in the stability of the system. Randomness ensures that each node has a healthy possibility of getting the incentive. The nodes are given a computationally hard hash puzzle and the first one to solve it gets to propose the next block. By solving the puzzle the node has made itself eligible for the incentive. This is known as the proof of work. The hash puzzle involves finding a hash value lesser than the target value decided by the network. To solve the puzzle, one has to find a random number––nonce. This should be hashed with the hash value (Merkle Root) of all the transactions in the block and the previous hash value. The resulting hash value is supposed to be less than the target value. The set of all possible hash values that are lesser than the target value is known as the target space.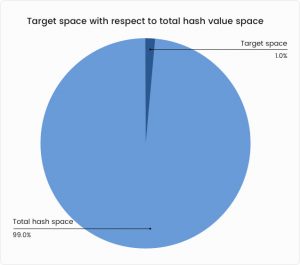 The target space will be less than 1% of the overall output space. This adds to the difficulty factor. The process of guessing this number is known as mining. The one who mines the block, or guesses the nonce, gets rewarded. Those nodes that engage in the process of mining are known as miners.
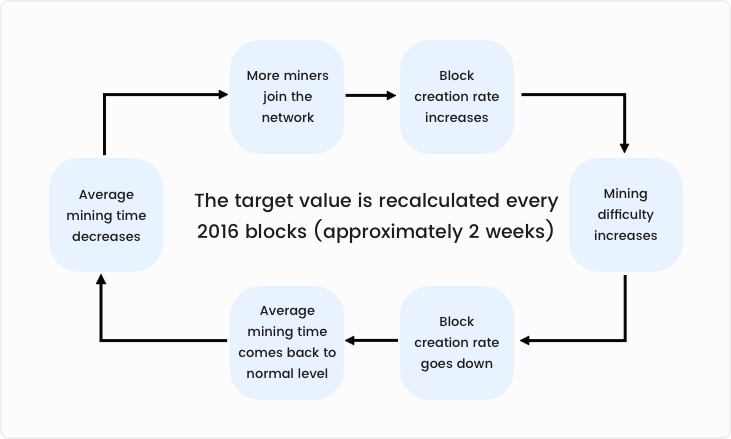
The network adjusts the target value and its difficulty in such a way that a new block is mined every 10 minutes. When more miners join the network and the block creation rate increases, the network readjusts the target value so that the block creation rate decreases and the loop continues.
The target space will be less than 1% of the overall output space. This adds to the difficulty factor. The process of guessing this number is known as mining. The one who mines the block, or guesses the nonce, gets rewarded. Those nodes that engage in the process of mining are known as miners.
The network adjusts the target value and its difficulty in such a way that a new block is mined every 10 minutes. When more miners join the network and the block creation rate increases, the network readjusts the target value so that the block creation rate decreases and the loop continues.
 The rate at which a node finds blocks depends on what other miners are doing. The probability of a miner mining the next block is proportional to the fraction of the global hash power that the node controls. Verifying the result is easy. The miner who mines the block must attach the nonce value in the proposed block. The other nodes only need to verify that the hash value of the block is less than the target value.
The rate at which a node finds blocks depends on what other miners are doing. The probability of a miner mining the next block is proportional to the fraction of the global hash power that the node controls. Verifying the result is easy. The miner who mines the block must attach the nonce value in the proposed block. The other nodes only need to verify that the hash value of the block is less than the target value.
Incentive Mechanisms
The system relies on honest nodes. In order to promote honesty, an incentive mechanism was introduced in Bitcoin. There are two ways in which honest nodes get rewarded:- Block reward
- Transaction fee

